9 Ways That Phishers Avoid Detection in Web3

Phishing is a deceptive practice where attackers impersonate legitimate brands, people, and other entities, to steal sensitive information.
Phishing is a significant threat in the Web3 space because transactions are irreversible in blockchain systems. Unlike the centralized financial systems we typically use today, there’s no way to cancel a fraudulent transaction. Many users are also new to Web3 technologies and don’t fully understand the complex digital machinery that they are interacting with, which makes it easier for scammers to exploit them and steal their assets.
Phishers have rapidly adapted their tactics to exploit the unique constraints of Web3 technology. Self-sovereign identity and digital assets mean that individuals and companies are responsible for their own digital risk making it crucial for everyone in the crypto space to understand how these threats evolve.
By knowing the most common strategies used by phishers to avoid detection, you can better guide your security efforts to protect your community and their assets. Understanding these tactics helps you to develop effective security countermeasures that keep you and your organization one step ahead of scammers.
9 Strategies That Phishers Use to Avoid Detection in Web3
Let’s dive into the top 9 strategies phishers are using today to evade detection in the Web3 space.
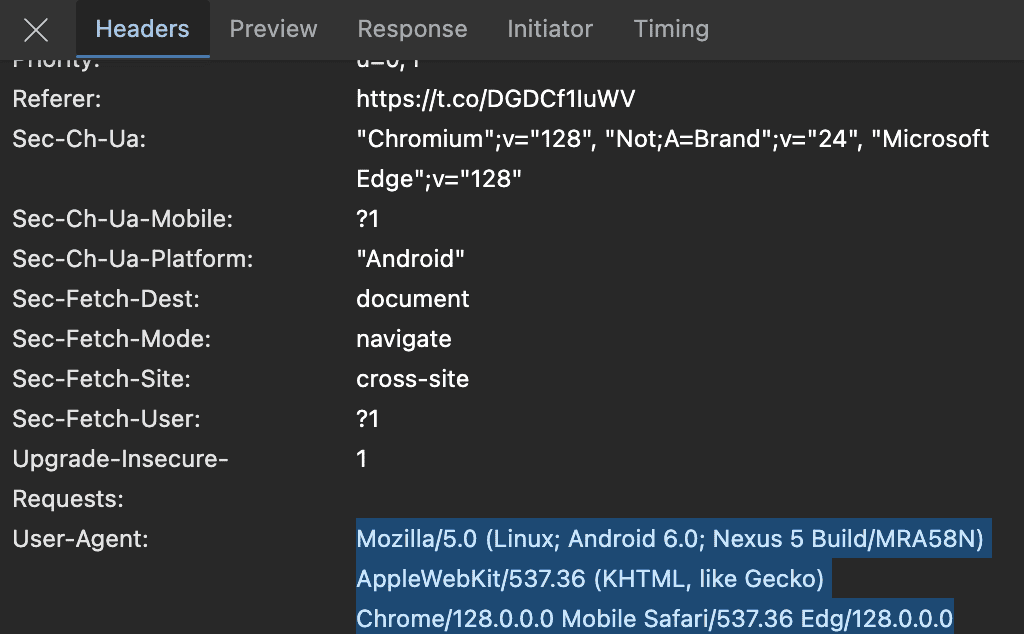
1. User-Agent Sniffing
User-agent sniffing is when websites check what type of browser or device a user is on by looking at a piece of data called the “user-agent string.” This string tells them what browser version, operating system, and device you’re using.
Websites often use this information to show you content that is most relevant to you. For example, a site that allows you to download multiple versions of a desktop app like Slack or 1Password might detect your operating system using the user-agent string and recommend that you download the version that is most compatible with your system.
User-agent strings are also used by search engine crawlers and other bots to identify themselves to web pages. For example, Google’s crawler identifies itself to web servers it crawls as “GoogleBot”. Knowing this, many websites detect this string and serve optimized versions of their pages, without additional content like ads or pop-ups, to rank higher on search engines.
While most websites use user-agent sniffing for legitimate purposes, scammers can use it to trick you by serving benign content to bots, and malicious content to real users. They can also detect if someone is using an in-app browser, and tailor the content those users see. With user-agent sniffing, scammers can trick users into clicking a link preview on X (formerly Twitter) or Slack that looks 100% legitimate, but when they actually click the link, it actually takes them to a malicious webpage.
2. Referer Sniffing
Similar to user-agent sniffing, referrer sniffing involves scammers examining the “Referer” HTTP header to determine the origin of a website request. This header provides information about the site or page that directed a user to the current page, enabling scammers to track user behavior across websites.
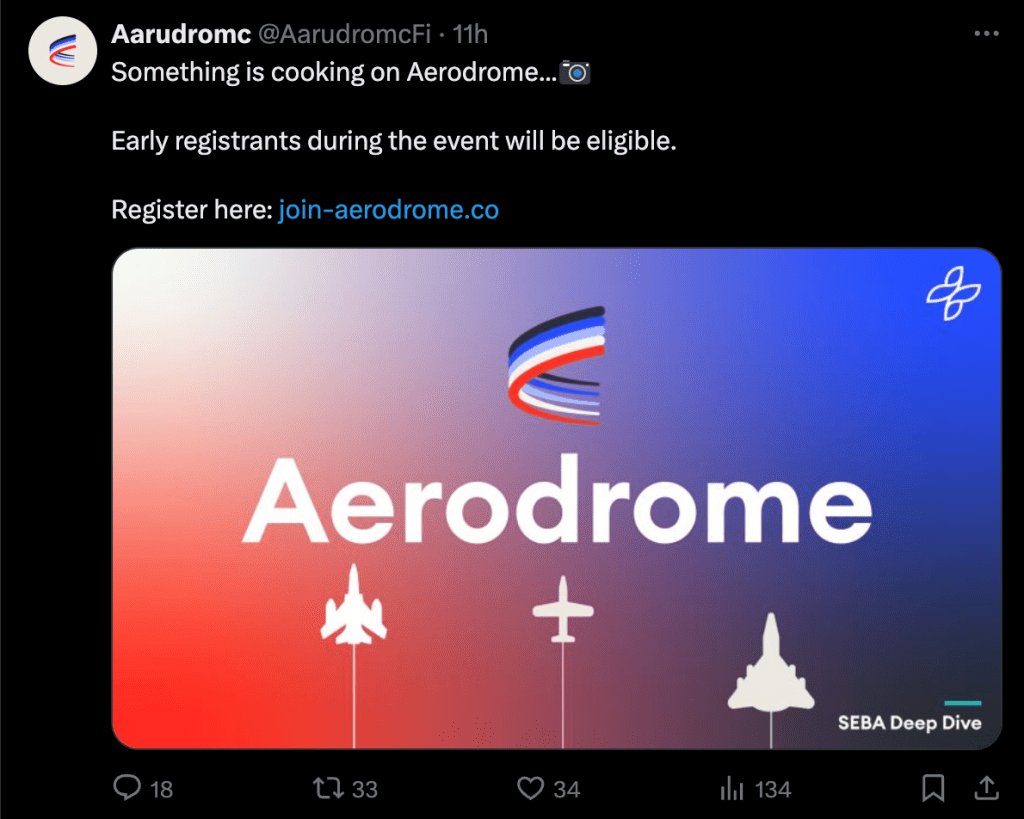
This information makes it possible for scammers to decide whether to show their scam content or hide it based on where they think the request is coming from. For example, they might show a fake NFT mint scam page only to real users who accessed the webpage by clicking on a link from x.com or through a Google Ad, but when a security researcher types in the URL by hand in their web browser, the site appears to be a benign WordPress blog for cat-lovers 🐈.
3. URL Confusion
URL confusion is a cloaking strategy that takes advantage of bugs in the algorithms that interpret web addresses. While it looks quite simple, URLs actually have a very complex schema including variations in:
- Protocols
- Username & Password
- Hostnames & IP Addresses
- Ports
- Paths
- Query Parameters
- Fragments
- Encodings
When you type a URL into your browser, there’s a parsing process which takes place to break apart the URL into its standardized parts. And while there are formal specifications for how URLs are structured, it’s quite common to see differences in implementations across different browsers, libraries, and servers either due to backwards compatibility requirements or to help deal with user error. For example, Google Chrome normalizes additional slashes in the protocol scheme separator, but other tools like Python’s urllib do not.
| Type | Input | Google Chrome | Node.js URL | Python urllib.parse | cURL |
| Scheme | example.com |
Host: example.com Path: None |
Invalid URL |
Host: None Path: example.com |
Host: example.com Path: None |
| Slash | http:///example.com |
Host: example.com Path: None |
Host: example.com Path: None |
Host: None Path: /example.com |
Host: example.com Path: None |
| Backslash | http:\\example.com |
Host: example.com Path: None |
Host: example.com Path: None |
Host: None Path: \\example.com |
Invalid URL |
| URL-Encoding | http://%65%78%61%6d%70%6c%65%2e%63%6f%6d |
Host: example.com Path: None |
Host: example.com Path: None |
Host: %65%78%61%6d%70%6c%65%2e%63%6f%6d Path: None |
Host: example.com Path: None |
Scammers exploit bugs and incompatibilities in URL parsing libraries (commonly vulnerabilities in Regex matching) to overload or mislead security tools that parse URLs as part of their analysis process.
4. Cloudflare Bot Protection
Phishers have found a clever way to dodge detection by taking advantage of Cloudflare’s bot protection tools. These tools, designed to keep malicious bots out, ironically end up working in the scammers’ favor.
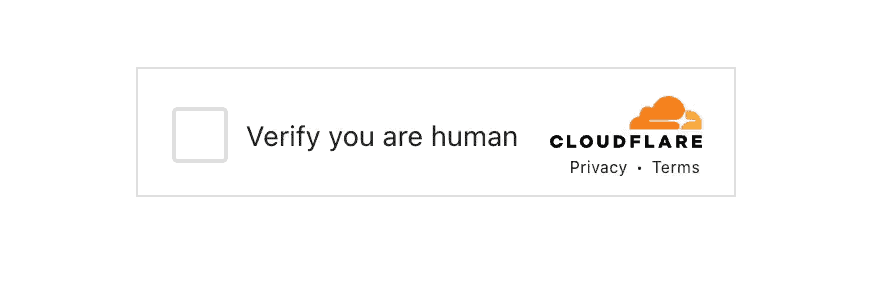
By using them, phishers can stop security scanners from crawling their websites, which means that many automated systems meant to catch these scams are blocked before they can even get a peek. This tactic helps phishers keep their fraudulent sites up and running longer, making it tougher for security teams to catch and shut them down quickly.
This example is a good reminder to security researchers that even with the tools we develop to defend against cyber threats, we need to think with an “adversarial mindset” of how these tools could be used against us one day.
5. Anti-Debugging
Anti-debugging is a strategy used by phishers to embed extra code into their JavaScript that can detect if a developer has their browser DevTools open. One of the ways this is done is by placing debugger statements throughout the script in sections of the code that execute in a loop. These debugger statements do nothing while the browser DevTools are closed, but when they are open, they trigger breakpoints in the execution of the script. This temporarily stalls the program and prevents it from continuing until the developer hits ‘Continue’.
This on its own is slightly annoying for security researchers, but phishing kit developers go one step further by carefully measuring the timing changes that happen when debugging is turned on.
If they detect something’s up, they can cause all sorts of headaches for researchers—crashing browser tabs, burying their malicious code deeper, or bombarding the developer with annoying permission requests. Anti-debugging is a sneaky tripwire that makes it challenging to uncover what phishers are up to.
6. Code Obfuscation
Scammers use code obfuscation to make their malicious code harder to detect, analyze, and understand. This technique will scramble or alter the code’s appearance without changing its functionality. This way, scammers can hide their intentions from security tools, researchers, and even other attackers.
Here’s a few reasons why scammers will often rely on code obfuscation:
- Evades Detection: Obfuscated code can bypass signature-based detection systems, like antivirus programs, that use known patterns or signatures to identify malicious code. By changing the code’s structure, scammers can avoid being flagged by these tools.
- Delays Analysis: Security researchers and analysts often reverse-engineer malware to understand how it works and develop countermeasures. Obfuscation makes this much more difficult and time-consuming, because it conceals the code’s logic and control flow.
- Hiding Malicious Intent: Obfuscation can mask critical parts of the code, like payload delivery mechanisms, data exfiltration routines, or command-and-control server addresses. This makes it harder to identify what the code is doing or where it’s sending data.
- Targeted Attacks: In more sophisticated attacks, scammers might tailor obfuscated code to specific environments. This makes it difficult for analysts who are not in that environment to fully understand the code’s behavior.
Code obfuscation on its own is not an inherently malicious practice. In fact, many web-based games and video-hosting sites make use of obfuscation to make it harder to reverse engineer their client-side JavaScript code which contains trade secrets that they don’t want competitors to steal or business logic they don’t want users to tamper with.
Phishing kit developers typically apply advanced techniques of code obfuscation like dead code injection, control flow flattening, unicode escaping, expression substitution, string arrays, and many more exotic forms of indirection to thwart researchers. There are many off-the-shelf and proprietary tools for performing code obfuscation in an automated fashion, and so virtually all viable phishing kits used in Web3 today come with this baked in as a “feature”.
7. Honeypots
Honeypots are a technique that phishers use to identify security bots and analysts. They will allow some of their phishing sites to be caught – on purpose – with an ulterior motive.
When bots and analysts visit the site, the phishers gather info on them, like their IP addresses, user agents, and even wallet addresses. With this data, the phishers create a blocklist, essentially stopping these specific security tools and analysts from ever detecting their future scams.
Honeypots are a strategy that enables scammers to stay one step ahead, making it harder for researchers to consistently identify threats from bad actors. Again, like the Cloudflare Bot Protection technique mentioned above, this is an example where a tactic that is often used by security researchers themselves to lure threats into their detectors can be used against us to help cloak bad actors.
8. Dynamic Code Generation
Dynamic code generation is a phishing technique that uses a sophisticated Command & Control setup that tailors scams specifically for each visitor. When someone lands on one of these phishing sites, the server can whip up a custom scam on the spot, including new smart contracts or an entire unique phishing site just for that person.
Dynamic code generation is also used to switch up the website’s branding and visual elements for each visitor. Phishing kits will often have multiple scams targeting different brands hosted on the same underlying infrastructure, and may dynamically switch the contents of the webpage or the requested smart contract transaction based on:
- How the user reached the server
- What’s in their wallet (NFTs, tokens, etc.)
- The user’s prior transaction history
At the moment, most of the phishing attacks we’ve analyzed are generating these variations at build time and some at transaction time. However, there’s a growing worry among researchers that the commoditization of Large Language Models (LLMs) and other generative algorithms capable of generating working code may enable a new wave of dynamic code generation techniques that are even more convincing and even harder for researchers to develop signatures for.
9. IP Geofencing and Filtering
IP geofencing and filtering makes it possible for phishers to control who can access their scam sites based on where they are located. They set up geographic barriers that block visitors from regions known for having strong security firms or active law enforcement agencies.
By doing this, they make it much harder for security experts and investigators in those areas to even reach their sites, let alone analyze or shut them down. It’s a move that helps them avoid detection, and keeps their scams running longer without intervention.
Web3 Security Practices to Keep Top of Mind
Understanding the ways that phishers avoid detection helps to protect you, your brand, and your community. With an understanding of the techniques scammers are using, you can create a security strategy that keeps your organization and your users safe.
Keep these two tips top of mind, for staying protected in Web3:
-
Stay Informed and Educated:
Be sure to regularly update your knowledge on emerging threats and scams in the Web3 space by following trusted sources.
-
Use Reputable Wallets and Security Tools:
Choose wallets with a strong security track record, and use security platforms like ChainPatrol to detect and avoid phishing sites.
Are you ready to protect your brand and community? Book a ChainPatrol demo to learn how we can help.