Changelog
Changelog
Changelog
Stay up-to-date with ChainPatrol! Explore the latest updates, bug fixes, and new features we've added.
This month, we’ve introduced several improvements to better protect your brand by enhancing monitoring, reviewing, and takedowns of malicious threats.
Automated Takedowns for Google Sites/Forms, Cloudflare, and IPFS
Our automated takedown system now extends to Google Sites, Google Forms, Cloudflare-hosted pages, and IPFS. Once an asset is blocked, ChainPatrol files a takedown request without any manual steps to the correct domain or hosting provider. This streamlined approach helps remove harmful content faster and minimizes time to remediation.
We’re focused on a goal of reaching 90% automation of takedown operations with <0.1% false positive rate by the end of 2025. We started the year at ~18% automation, and with these and other changes we’ve shipped, we’re now at ~46%. Heading into Q2, you can expect us to continue on this goal with improvements to our liveness checking and detecting cases where human intervention is needed to resolve takedowns faster.

Enhanced Reporting with AI & Confidence Scoring
We’ve introduced a broader range of detection rules to improve accuracy and reduce the need for manual reviews. Offline (“dead”) assets are now placed on a watchlist, so if they come back online, the system automatically reassesses them. We’ve also optimized data handling and infrastructure to speed up threat evaluations and ensure more efficient protection.

New Reviewing Rules
We’ve expanded our automated analysis to catch a wider range of threats, including phishing attempts like seed phrase requests, obfuscated code, and suspicious Twitter accounts. These automated rules lighten the workload for our threat analysts and human reviewers, letting them focus on more complex or high-priority cases.

Refined Threats Page Experience
We refreshed the Threats Page to fix some of the UI/UX paper cuts. We added a skeleton loader and improved error handling with clear instructions and retry options. Page and filter changes also update instantly, giving you a smoother, more responsive way to track and address active threats.
In April, we’ll be hunting down more UI/UX issues and performance bugs to make our dashboards faster to load and easier to use.
This month, we’ve introduced several improvements to better protect your brand by enhancing monitoring, reviewing, and takedowns of malicious threats.
Automated Takedowns for Google Sites/Forms, Cloudflare, and IPFS
Our automated takedown system now extends to Google Sites, Google Forms, Cloudflare-hosted pages, and IPFS. Once an asset is blocked, ChainPatrol files a takedown request without any manual steps to the correct domain or hosting provider. This streamlined approach helps remove harmful content faster and minimizes time to remediation.
We’re focused on a goal of reaching 90% automation of takedown operations with <0.1% false positive rate by the end of 2025. We started the year at ~18% automation, and with these and other changes we’ve shipped, we’re now at ~46%. Heading into Q2, you can expect us to continue on this goal with improvements to our liveness checking and detecting cases where human intervention is needed to resolve takedowns faster.

Enhanced Reporting with AI & Confidence Scoring
We’ve introduced a broader range of detection rules to improve accuracy and reduce the need for manual reviews. Offline (“dead”) assets are now placed on a watchlist, so if they come back online, the system automatically reassesses them. We’ve also optimized data handling and infrastructure to speed up threat evaluations and ensure more efficient protection.

New Reviewing Rules
We’ve expanded our automated analysis to catch a wider range of threats, including phishing attempts like seed phrase requests, obfuscated code, and suspicious Twitter accounts. These automated rules lighten the workload for our threat analysts and human reviewers, letting them focus on more complex or high-priority cases.

Refined Threats Page Experience
We refreshed the Threats Page to fix some of the UI/UX paper cuts. We added a skeleton loader and improved error handling with clear instructions and retry options. Page and filter changes also update instantly, giving you a smoother, more responsive way to track and address active threats.
In April, we’ll be hunting down more UI/UX issues and performance bugs to make our dashboards faster to load and easier to use.
This month, we’ve introduced several improvements to better protect your brand by enhancing monitoring, reviewing, and takedowns of malicious threats.
Automated Takedowns for Google Sites/Forms, Cloudflare, and IPFS
Our automated takedown system now extends to Google Sites, Google Forms, Cloudflare-hosted pages, and IPFS. Once an asset is blocked, ChainPatrol files a takedown request without any manual steps to the correct domain or hosting provider. This streamlined approach helps remove harmful content faster and minimizes time to remediation.
We’re focused on a goal of reaching 90% automation of takedown operations with <0.1% false positive rate by the end of 2025. We started the year at ~18% automation, and with these and other changes we’ve shipped, we’re now at ~46%. Heading into Q2, you can expect us to continue on this goal with improvements to our liveness checking and detecting cases where human intervention is needed to resolve takedowns faster.

Enhanced Reporting with AI & Confidence Scoring
We’ve introduced a broader range of detection rules to improve accuracy and reduce the need for manual reviews. Offline (“dead”) assets are now placed on a watchlist, so if they come back online, the system automatically reassesses them. We’ve also optimized data handling and infrastructure to speed up threat evaluations and ensure more efficient protection.

New Reviewing Rules
We’ve expanded our automated analysis to catch a wider range of threats, including phishing attempts like seed phrase requests, obfuscated code, and suspicious Twitter accounts. These automated rules lighten the workload for our threat analysts and human reviewers, letting them focus on more complex or high-priority cases.

Refined Threats Page Experience
We refreshed the Threats Page to fix some of the UI/UX paper cuts. We added a skeleton loader and improved error handling with clear instructions and retry options. Page and filter changes also update instantly, giving you a smoother, more responsive way to track and address active threats.
In April, we’ll be hunting down more UI/UX issues and performance bugs to make our dashboards faster to load and easier to use.
Mar 6, 2025
Here’s a roundup of the most relevant product updates the ChainPatrol team rolled out in February. We've been busy making takedowns faster, reducing manual work, and giving you more control over your assets.
Vercel Integration
ChainPatrol now integrates with Vercel, a leading platform for hosting and deploying web applications. This integration helps us track legitimate Vercel deployments, ensuring that our takedown efforts focus only on malicious or scam sites—without mistakenly flagging your legitimate projects.
If you use Vercel, this means no false positives and no unnecessary disruptions to your deployments while we continue protecting your brand. To take advantage of this feature, simply install the integration at this link.

Teachable Automated Takedowns
Teachable.com is a website for selling courses and other educational products. Like other content hosting sites such as Gitbook and Webflow, we’ve seen a rise in its abuse for hosting malicious content targeting Web3 brands.
This month, we worked on making takedown requests for Teachable assets fully automated. Now when a Teachable asset is blocked, a takedown email is automatically sent to Teachable without any need for manual intervention. This update ensures immediate action on blocked assets, significantly reducing the workload for our staff.
With less manual effort required, enforcement becomes faster, compliance improves, and the entire process becomes more efficient.

Organization Asset Removal
Organization admins now have the ability to delete assets from their organization’s asset list. Previously, once an asset was added, it couldn’t be removed easily, leading to clutter and potential mistakes accumulating over time.
With this new functionality, admins have greater control over their organization's assets. The update allows you to clean up unwanted or mistakenly added assets, ensuring that asset lists remain organized and relevant.
By reducing the reliance on support teams or workaround solutions, this change streamlines asset management. To use this feature, admins can navigate to Organization Settings, then select Organization Assets to manage and remove assets as needed.
Keeping organization assets up-to-date means more accurate detections, scans, and automated enforcement actions, and faster time to remediation.

Semi-Automated Takedowns Refile for Medium
For some providers, multiple takedown requests are required to successfully remove an asset. While the initial takedown requests are largely automated, the process of refiling has historically been a manual task.
This update introduces a semi-automated approach for refiling takedown requests specifically for Medium. Using our refiling tool, the system now handles follow-up requests, significantly speeding up the takedown process.
By reducing the need for manual intervention, this update not only improves efficiency but also minimizes human error and delays. More consistent enforcement of takedown requests ensures a smoother experience for everyone.

Have questions about ChainPatrol’s February product update? Feel free to contact your customer success representative, or email us.
Here’s a roundup of the most relevant product updates the ChainPatrol team rolled out in February. We've been busy making takedowns faster, reducing manual work, and giving you more control over your assets.
Vercel Integration
ChainPatrol now integrates with Vercel, a leading platform for hosting and deploying web applications. This integration helps us track legitimate Vercel deployments, ensuring that our takedown efforts focus only on malicious or scam sites—without mistakenly flagging your legitimate projects.
If you use Vercel, this means no false positives and no unnecessary disruptions to your deployments while we continue protecting your brand. To take advantage of this feature, simply install the integration at this link.

Teachable Automated Takedowns
Teachable.com is a website for selling courses and other educational products. Like other content hosting sites such as Gitbook and Webflow, we’ve seen a rise in its abuse for hosting malicious content targeting Web3 brands.
This month, we worked on making takedown requests for Teachable assets fully automated. Now when a Teachable asset is blocked, a takedown email is automatically sent to Teachable without any need for manual intervention. This update ensures immediate action on blocked assets, significantly reducing the workload for our staff.
With less manual effort required, enforcement becomes faster, compliance improves, and the entire process becomes more efficient.

Organization Asset Removal
Organization admins now have the ability to delete assets from their organization’s asset list. Previously, once an asset was added, it couldn’t be removed easily, leading to clutter and potential mistakes accumulating over time.
With this new functionality, admins have greater control over their organization's assets. The update allows you to clean up unwanted or mistakenly added assets, ensuring that asset lists remain organized and relevant.
By reducing the reliance on support teams or workaround solutions, this change streamlines asset management. To use this feature, admins can navigate to Organization Settings, then select Organization Assets to manage and remove assets as needed.
Keeping organization assets up-to-date means more accurate detections, scans, and automated enforcement actions, and faster time to remediation.

Semi-Automated Takedowns Refile for Medium
For some providers, multiple takedown requests are required to successfully remove an asset. While the initial takedown requests are largely automated, the process of refiling has historically been a manual task.
This update introduces a semi-automated approach for refiling takedown requests specifically for Medium. Using our refiling tool, the system now handles follow-up requests, significantly speeding up the takedown process.
By reducing the need for manual intervention, this update not only improves efficiency but also minimizes human error and delays. More consistent enforcement of takedown requests ensures a smoother experience for everyone.

Have questions about ChainPatrol’s February product update? Feel free to contact your customer success representative, or email us.
Here’s a roundup of the most relevant product updates the ChainPatrol team rolled out in February. We've been busy making takedowns faster, reducing manual work, and giving you more control over your assets.
Vercel Integration
ChainPatrol now integrates with Vercel, a leading platform for hosting and deploying web applications. This integration helps us track legitimate Vercel deployments, ensuring that our takedown efforts focus only on malicious or scam sites—without mistakenly flagging your legitimate projects.
If you use Vercel, this means no false positives and no unnecessary disruptions to your deployments while we continue protecting your brand. To take advantage of this feature, simply install the integration at this link.

Teachable Automated Takedowns
Teachable.com is a website for selling courses and other educational products. Like other content hosting sites such as Gitbook and Webflow, we’ve seen a rise in its abuse for hosting malicious content targeting Web3 brands.
This month, we worked on making takedown requests for Teachable assets fully automated. Now when a Teachable asset is blocked, a takedown email is automatically sent to Teachable without any need for manual intervention. This update ensures immediate action on blocked assets, significantly reducing the workload for our staff.
With less manual effort required, enforcement becomes faster, compliance improves, and the entire process becomes more efficient.

Organization Asset Removal
Organization admins now have the ability to delete assets from their organization’s asset list. Previously, once an asset was added, it couldn’t be removed easily, leading to clutter and potential mistakes accumulating over time.
With this new functionality, admins have greater control over their organization's assets. The update allows you to clean up unwanted or mistakenly added assets, ensuring that asset lists remain organized and relevant.
By reducing the reliance on support teams or workaround solutions, this change streamlines asset management. To use this feature, admins can navigate to Organization Settings, then select Organization Assets to manage and remove assets as needed.
Keeping organization assets up-to-date means more accurate detections, scans, and automated enforcement actions, and faster time to remediation.

Semi-Automated Takedowns Refile for Medium
For some providers, multiple takedown requests are required to successfully remove an asset. While the initial takedown requests are largely automated, the process of refiling has historically been a manual task.
This update introduces a semi-automated approach for refiling takedown requests specifically for Medium. Using our refiling tool, the system now handles follow-up requests, significantly speeding up the takedown process.
By reducing the need for manual intervention, this update not only improves efficiency but also minimizes human error and delays. More consistent enforcement of takedown requests ensures a smoother experience for everyone.

Have questions about ChainPatrol’s February product update? Feel free to contact your customer success representative, or email us.
Feb 11, 2025
Here’s a roundup of the most relevant product updates the ChainPatrol team rolled out in January. From real-time webhooks and seamless API integrations to smarter detection and an automated Medium takedown system, these updates are all about improving accuracy, efficiency, and user experience.
Webhooks for Real-Time Blocklist Updates
You can now set up webhooks to get notified the moment ChainPatrol updates its global blocklist. This means you’ll have access to the latest scam data within seconds—perfect for keeping your integrations up to date in real-time. To start using webhooks, head to the Webhooks section in your ChainPatrol dashboard settings.

API Keys for Seamless Integrations
You can now programmatically interact with ChainPatrol through our integrations using API Keys. These keys let us verify and identify your requests, unlocking more features and deeper integration with the ChainPatrol app. To get started, generate your API Key in the API Keys section of your ChainPatrol dashboard settings.

Smarter Detection & Fewer False Positives
We've improved ChainPatrol's detection flow to reduce false positives and make enforcement more accurate. Now, enforcement won’t apply to social media assets if the organization has none, legitimacy checks help verify popular YouTube channels and videos, and our browser extension has enhanced scanning capabilities. These updates mean fewer interruptions for legitimate users while maintaining strong protection.
Enhanced Medium Threat Detection & Automated Takedowns
ChainPatrol now features a two-part automated system for removing scam content on Medium. When fraudulent content is blocked, an immediate UI report is generated, and every three hours, a batch email takedown request is sent—reducing manual effort while keeping scam removal efficient.
The system handles both methods without manual intervention, but manual triggers remain available for urgent cases. This automated system streamlines enforcement, minimizes false positives, and ensures ChainPatrol’s brand protection is more comprehensive than ever.

Public ChainPatrol Status Page
We’ve launched a public status page to keep you informed about the health of our services, including our Dashboard, APIs, and Website. If there’s an outage or disruption, you can check for real-time updates from our team.
The status page helps you quickly determine whether an issue is affecting only you or if it’s a broader outage. API integrators can use it to check for service disruptions when they spot errors in their logs. Plus, it keeps you informed about scheduled maintenance, outages, and performance issues—all in one place.
You can visit the status page anytime you experience issues with the app or API. We’ll post real-time updates, and if you need urgent support, you can use the Get in Touch button to contact our team immediately. View the Status Page, here.

Have questions about ChainPatrol’s January product update? Feel free to contact your customer success representative, or email us.
Here’s a roundup of the most relevant product updates the ChainPatrol team rolled out in January. From real-time webhooks and seamless API integrations to smarter detection and an automated Medium takedown system, these updates are all about improving accuracy, efficiency, and user experience.
Webhooks for Real-Time Blocklist Updates
You can now set up webhooks to get notified the moment ChainPatrol updates its global blocklist. This means you’ll have access to the latest scam data within seconds—perfect for keeping your integrations up to date in real-time. To start using webhooks, head to the Webhooks section in your ChainPatrol dashboard settings.

API Keys for Seamless Integrations
You can now programmatically interact with ChainPatrol through our integrations using API Keys. These keys let us verify and identify your requests, unlocking more features and deeper integration with the ChainPatrol app. To get started, generate your API Key in the API Keys section of your ChainPatrol dashboard settings.

Smarter Detection & Fewer False Positives
We've improved ChainPatrol's detection flow to reduce false positives and make enforcement more accurate. Now, enforcement won’t apply to social media assets if the organization has none, legitimacy checks help verify popular YouTube channels and videos, and our browser extension has enhanced scanning capabilities. These updates mean fewer interruptions for legitimate users while maintaining strong protection.
Enhanced Medium Threat Detection & Automated Takedowns
ChainPatrol now features a two-part automated system for removing scam content on Medium. When fraudulent content is blocked, an immediate UI report is generated, and every three hours, a batch email takedown request is sent—reducing manual effort while keeping scam removal efficient.
The system handles both methods without manual intervention, but manual triggers remain available for urgent cases. This automated system streamlines enforcement, minimizes false positives, and ensures ChainPatrol’s brand protection is more comprehensive than ever.

Public ChainPatrol Status Page
We’ve launched a public status page to keep you informed about the health of our services, including our Dashboard, APIs, and Website. If there’s an outage or disruption, you can check for real-time updates from our team.
The status page helps you quickly determine whether an issue is affecting only you or if it’s a broader outage. API integrators can use it to check for service disruptions when they spot errors in their logs. Plus, it keeps you informed about scheduled maintenance, outages, and performance issues—all in one place.
You can visit the status page anytime you experience issues with the app or API. We’ll post real-time updates, and if you need urgent support, you can use the Get in Touch button to contact our team immediately. View the Status Page, here.

Have questions about ChainPatrol’s January product update? Feel free to contact your customer success representative, or email us.
Here’s a roundup of the most relevant product updates the ChainPatrol team rolled out in January. From real-time webhooks and seamless API integrations to smarter detection and an automated Medium takedown system, these updates are all about improving accuracy, efficiency, and user experience.
Webhooks for Real-Time Blocklist Updates
You can now set up webhooks to get notified the moment ChainPatrol updates its global blocklist. This means you’ll have access to the latest scam data within seconds—perfect for keeping your integrations up to date in real-time. To start using webhooks, head to the Webhooks section in your ChainPatrol dashboard settings.

API Keys for Seamless Integrations
You can now programmatically interact with ChainPatrol through our integrations using API Keys. These keys let us verify and identify your requests, unlocking more features and deeper integration with the ChainPatrol app. To get started, generate your API Key in the API Keys section of your ChainPatrol dashboard settings.

Smarter Detection & Fewer False Positives
We've improved ChainPatrol's detection flow to reduce false positives and make enforcement more accurate. Now, enforcement won’t apply to social media assets if the organization has none, legitimacy checks help verify popular YouTube channels and videos, and our browser extension has enhanced scanning capabilities. These updates mean fewer interruptions for legitimate users while maintaining strong protection.
Enhanced Medium Threat Detection & Automated Takedowns
ChainPatrol now features a two-part automated system for removing scam content on Medium. When fraudulent content is blocked, an immediate UI report is generated, and every three hours, a batch email takedown request is sent—reducing manual effort while keeping scam removal efficient.
The system handles both methods without manual intervention, but manual triggers remain available for urgent cases. This automated system streamlines enforcement, minimizes false positives, and ensures ChainPatrol’s brand protection is more comprehensive than ever.

Public ChainPatrol Status Page
We’ve launched a public status page to keep you informed about the health of our services, including our Dashboard, APIs, and Website. If there’s an outage or disruption, you can check for real-time updates from our team.
The status page helps you quickly determine whether an issue is affecting only you or if it’s a broader outage. API integrators can use it to check for service disruptions when they spot errors in their logs. Plus, it keeps you informed about scheduled maintenance, outages, and performance issues—all in one place.
You can visit the status page anytime you experience issues with the app or API. We’ll post real-time updates, and if you need urgent support, you can use the Get in Touch button to contact our team immediately. View the Status Page, here.

Have questions about ChainPatrol’s January product update? Feel free to contact your customer success representative, or email us.
Dec 18, 2024
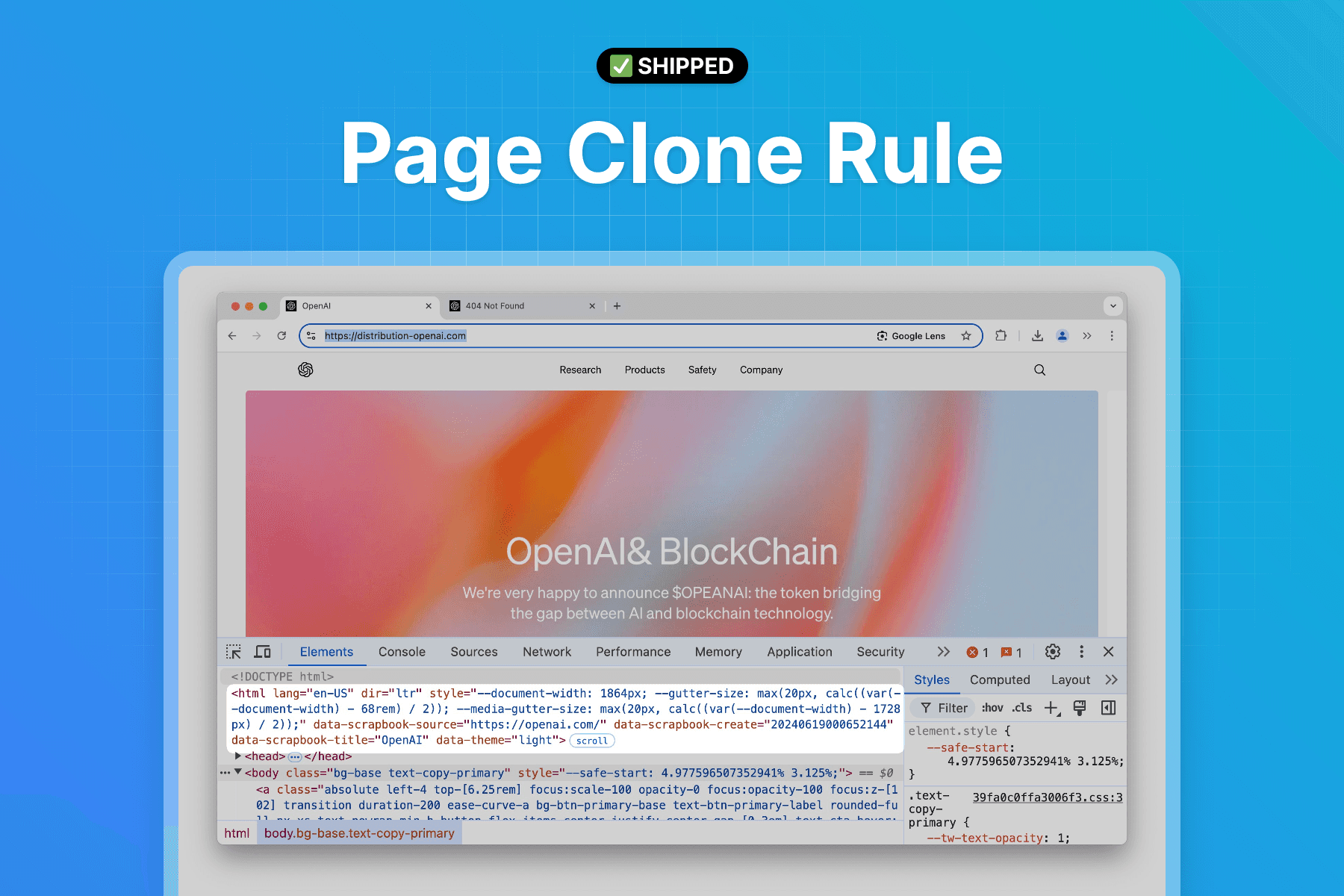
We’ve rolled out the Page Clone Rule, which enables us to detect indicators suggesting a webpage was generated using a page cloning tool.
Phishing pages are often created by cloning legitimate website landing pages and embedding a wallet drainer script. During this process, these page cloning tools leave behind specific indicators that give our system high confidence in identifying potentially malicious pages.
With our new page cloning detection rule, we’ve updated our system to provide an automated review process, resulting in faster detection and blocking of such websites.
We’ve rolled out the Page Clone Rule, which enables us to detect indicators suggesting a webpage was generated using a page cloning tool.
Phishing pages are often created by cloning legitimate website landing pages and embedding a wallet drainer script. During this process, these page cloning tools leave behind specific indicators that give our system high confidence in identifying potentially malicious pages.
With our new page cloning detection rule, we’ve updated our system to provide an automated review process, resulting in faster detection and blocking of such websites.
We’ve rolled out the Page Clone Rule, which enables us to detect indicators suggesting a webpage was generated using a page cloning tool.
Phishing pages are often created by cloning legitimate website landing pages and embedding a wallet drainer script. During this process, these page cloning tools leave behind specific indicators that give our system high confidence in identifying potentially malicious pages.
With our new page cloning detection rule, we’ve updated our system to provide an automated review process, resulting in faster detection and blocking of such websites.
Dec 10, 2024
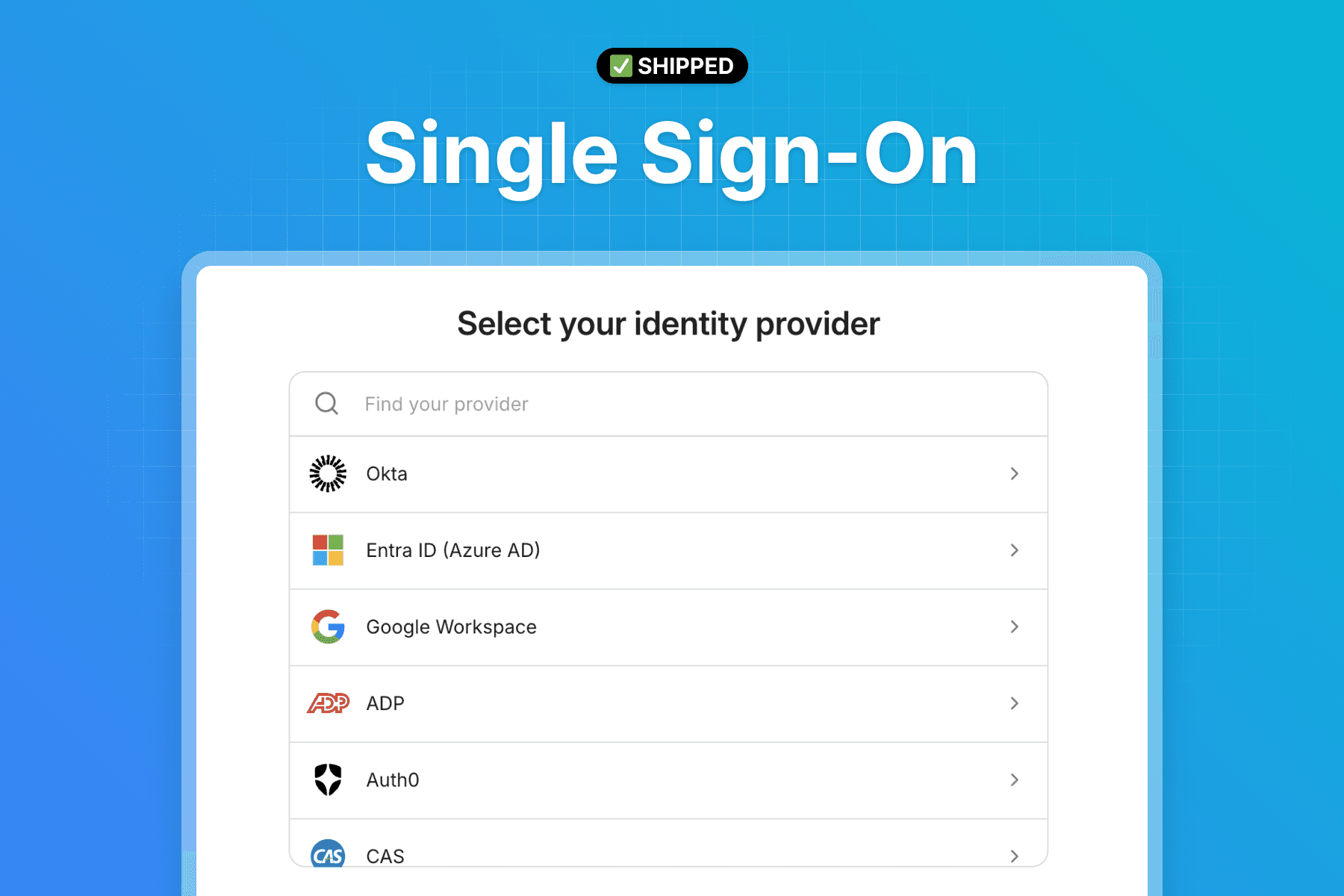
We’re enabling organizations to log in to ChainPatrol using their existing corporate identity provider, such as Okta, Google Workspace, OneLogin, and others, with single sign-on (SSO).
The introduction of SSO offers two major benefits:
It allows enterprise customers to enforce additional requirements and security rules within their identity provider of choice.
It provides more authentication options for ChainPatrol and simplifies the onboarding process for new users.
Please, reach out to us if you’d like to set up SSO for your organization.
We’re enabling organizations to log in to ChainPatrol using their existing corporate identity provider, such as Okta, Google Workspace, OneLogin, and others, with single sign-on (SSO).
The introduction of SSO offers two major benefits:
It allows enterprise customers to enforce additional requirements and security rules within their identity provider of choice.
It provides more authentication options for ChainPatrol and simplifies the onboarding process for new users.
Please, reach out to us if you’d like to set up SSO for your organization.
We’re enabling organizations to log in to ChainPatrol using their existing corporate identity provider, such as Okta, Google Workspace, OneLogin, and others, with single sign-on (SSO).
The introduction of SSO offers two major benefits:
It allows enterprise customers to enforce additional requirements and security rules within their identity provider of choice.
It provides more authentication options for ChainPatrol and simplifies the onboarding process for new users.
Please, reach out to us if you’d like to set up SSO for your organization.
Dec 3, 2024
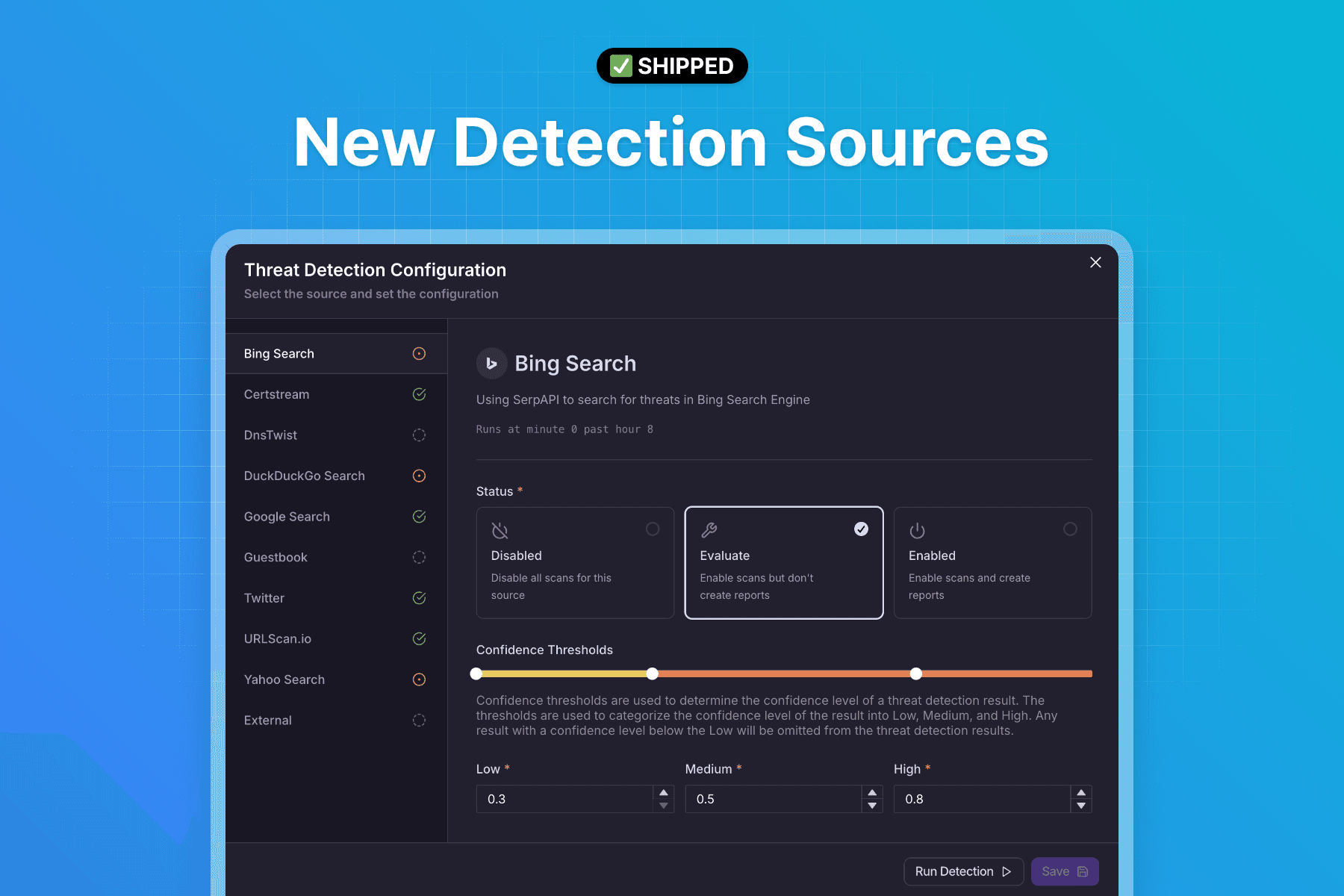
We've extended the reach of our detection by introducing four new sources:
Bing
Yahoo
DuckDuckGo
Guestbooks
By tapping into these new detection sources, we’ve enhanced protection across various search engines and hidden guestbook websites, where scammers often post their content. It enables us to improve both the quality and speed of detection for all organizations that are being monitored by ChainPatrol.
We've extended the reach of our detection by introducing four new sources:
Bing
Yahoo
DuckDuckGo
Guestbooks
By tapping into these new detection sources, we’ve enhanced protection across various search engines and hidden guestbook websites, where scammers often post their content. It enables us to improve both the quality and speed of detection for all organizations that are being monitored by ChainPatrol.
We've extended the reach of our detection by introducing four new sources:
Bing
Yahoo
DuckDuckGo
Guestbooks
By tapping into these new detection sources, we’ve enhanced protection across various search engines and hidden guestbook websites, where scammers often post their content. It enables us to improve both the quality and speed of detection for all organizations that are being monitored by ChainPatrol.
Nov 28, 2024
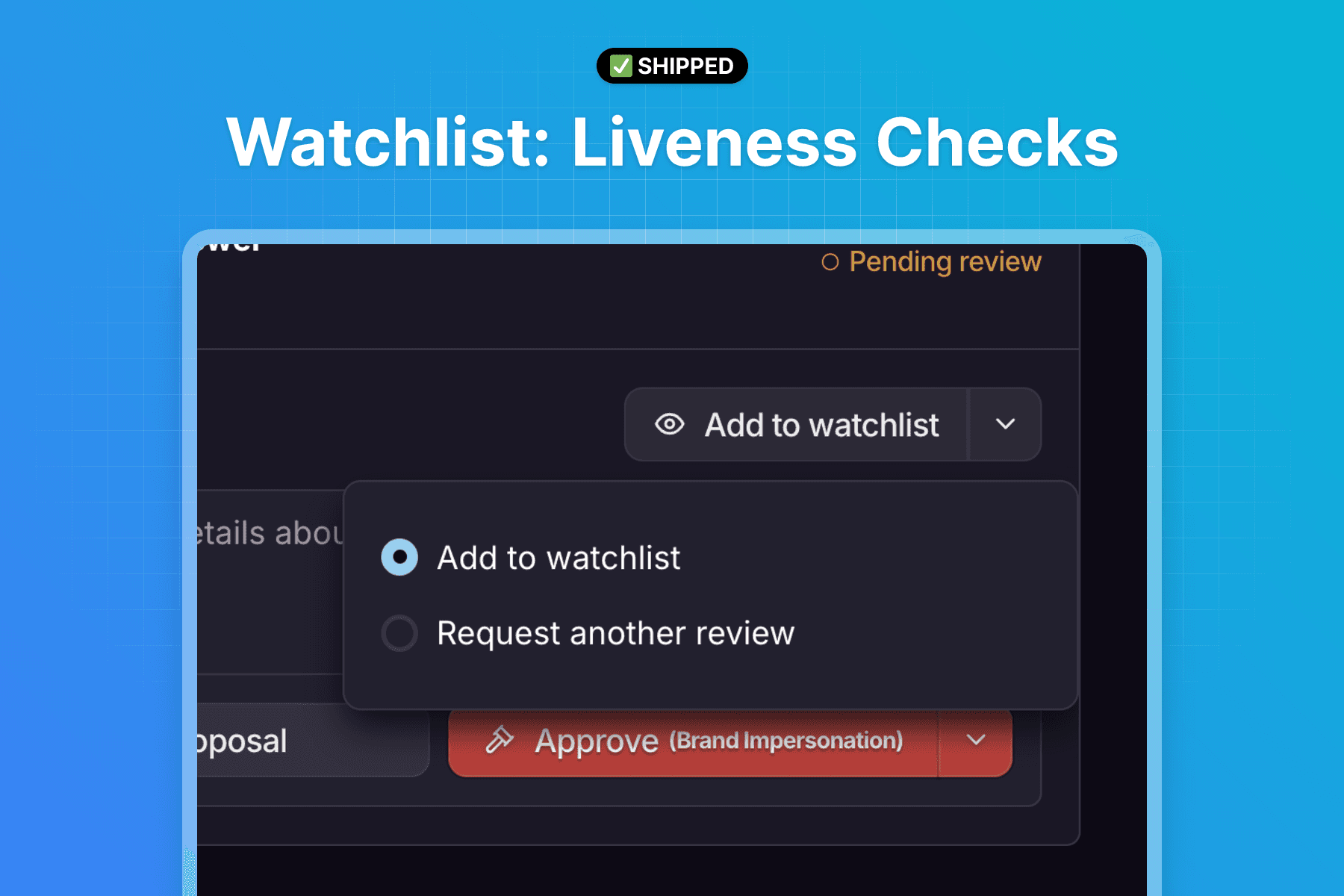
We’ve implemented an important update that involves periodically running checks on specific URL assets and extending our liveness checks with deeper analysis. This allows us to extract more information and make higher-quality decisions.
With this implementation, we are now conducting a more thorough and repetitive analysis of URLs that increases the quality of protection while reducing the chance of false positives. This also results in an increased frequency of asset updates, enabling our staff and automation to decide on the appropriate actions for certain assets.
We’ve implemented an important update that involves periodically running checks on specific URL assets and extending our liveness checks with deeper analysis. This allows us to extract more information and make higher-quality decisions.
With this implementation, we are now conducting a more thorough and repetitive analysis of URLs that increases the quality of protection while reducing the chance of false positives. This also results in an increased frequency of asset updates, enabling our staff and automation to decide on the appropriate actions for certain assets.
We’ve implemented an important update that involves periodically running checks on specific URL assets and extending our liveness checks with deeper analysis. This allows us to extract more information and make higher-quality decisions.
With this implementation, we are now conducting a more thorough and repetitive analysis of URLs that increases the quality of protection while reducing the chance of false positives. This also results in an increased frequency of asset updates, enabling our staff and automation to decide on the appropriate actions for certain assets.
We’ve introduced a new feature of the ChainPatrol Telegram Bot that allows users to flag malicious links in chat groups. Additionally, the reporting function now provides detailed information for links already in our system. If a link has already been blocked, the bot will display the current takedown progress to the user.
This new feature enhances the transparency and integration of ChainPatrol with Telegram, making it possible for the bot to include a community-facing feature. Additionally, users are kept informed about the progress of the takedown.
Note: You can check if your group settings are set up properly right here.
We’ve introduced a new feature of the ChainPatrol Telegram Bot that allows users to flag malicious links in chat groups. Additionally, the reporting function now provides detailed information for links already in our system. If a link has already been blocked, the bot will display the current takedown progress to the user.
This new feature enhances the transparency and integration of ChainPatrol with Telegram, making it possible for the bot to include a community-facing feature. Additionally, users are kept informed about the progress of the takedown.
Note: You can check if your group settings are set up properly right here.
We’ve introduced a new feature of the ChainPatrol Telegram Bot that allows users to flag malicious links in chat groups. Additionally, the reporting function now provides detailed information for links already in our system. If a link has already been blocked, the bot will display the current takedown progress to the user.
This new feature enhances the transparency and integration of ChainPatrol with Telegram, making it possible for the bot to include a community-facing feature. Additionally, users are kept informed about the progress of the takedown.
Note: You can check if your group settings are set up properly right here.
Load More
Load More
Load More

ChainPatrol
© 2025 ChainPatrol Inc., All Rights Reserved

ChainPatrol
© 2025 ChainPatrol Inc., All Rights Reserved

ChainPatrol
© 2025 ChainPatrol Inc., All Rights Reserved