How to Recover a Compromised X Account (2025)

If your X (formerly Twitter) account gets hacked, it can be stressful and frustrating. And if the account that’s been hacked is for your business, it can pose a risk to your clients and community.
Hackers target X accounts for various reasons—spreading scams, stealing personal information, or locking users out to demand a ransom. They like to target Web3 communities in particular, with the goal of draining crypto wallets.
Whether you have a high-profile account with thousands of followers or are just a casual user, you’re at risk of falling victim to these attacks.
Understanding how hackers gain access to X accounts and recognizing early warning signs are crucial steps in protecting yourself. If you suspect your account has been compromised, knowing what to do and how to regain control is essential.
In this blog, we’re covering the steps you should take if your X account is hacked and sharing practical tips to recover it. We’ll also share best practices to secure your account moving forward, so you can reduce the chances of a compromised account.
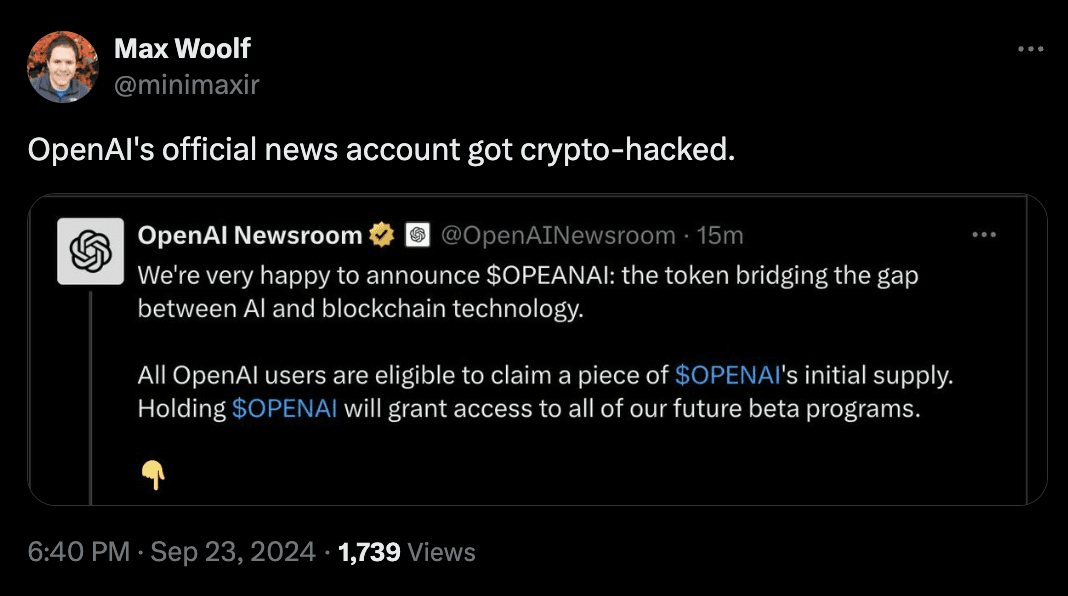
How Do X Accounts Get Hacked?
There are a couple common ways that X accounts are hacked. Knowing these will help you understand where the vulnerabilities with your account may be, and take action to mitigate those vulnerabilities.
Weak passwords are a major factor. Hackers can easily guess or crack simple passwords like “password123.” Using the same password across multiple platforms increases the risk, as stolen credentials from other sites can be reused.
Phishing attacks are another common method for hacking X accounts. Users are tricked into giving away login details by clicking on fake links or visiting counterfeit websites. Hackers often mimic X’s emails or support pages to deceive users.
Recent examples of X.com account hacks, including high-profile accounts like @LinusTech, have been linked to fake password reset and recovery emails
Lack of two-factor authentication (2FA) also makes accounts more vulnerable. Without 2FA, hackers only need your password to gain access to your account. 2FA adds an extra layer of protection by requiring a second step, such as entering a code from an authenticator app.
Malware or spyware on devices can steal login information. These programs are often installed unknowingly through unsafe downloads or visiting infected websites. And public Wi-Fi networks also pose a risk. Hackers can intercept data over unsecured connections, exposing login credentials.
Finally, third-party apps connected to X accounts can have weak security. If these apps are compromised, hackers can access the linked account.
Signs Your X Account is Compromised
So, how do you know when your X account has been compromised? There are a few tell-tale signs to look out for. If you notice any of the following, there’s a chance you’ve been hacked.
- Unusual Activity: You notice tweets, retweets, or likes that you didn’t make. Your followers may report receiving strange messages or DMs from your account. A sudden, unexplained drop in follower count can indicate malicious activity.
- Changed Account Information: Your profile details, such as your email, password, or username, have been changed without your knowledge.
- Login Issues: You’re suddenly logged out of your account and can’t log back in, even with the correct password. You may be receiving emails from X about unusual login attempts or account access.
- Password Reset Requests: You receive notifications for password reset attempts that you didn’t initiate. You might also notice login activity from devices or locations you don’t recognize.
If you notice any of these signs, take immediate action to recover your account.
How to Recover a Compromised X Account
If you’ve noticed signs that your X account may be compromised, you’ll want to take immediate action to regain control of it.
Step 1: Attempt to Log In
Start by attempting to log into your X account. It’s important to manually type in the URL for X (X.com) to navigate to the login page – don’t follow any links from email or chat. Scammers will often impersonate X support, so the best line of defense is to always manually navigate to the site.
If your password doesn’t work when you attempt to log in, go to the login screen and click “Forgot Password” to reset it. If this works, make sure to choose a strong password you haven’t used before.
Along with resetting your password, you’ll want to make sure your account’s email is secure and only you have access to it. You can change your email by going to Account settings on the X app or X.com.
You will also want to revoke access to your X account for unrecognized apps. Go to Apps in your settings and remove access for any third-party app you don’t recognize.
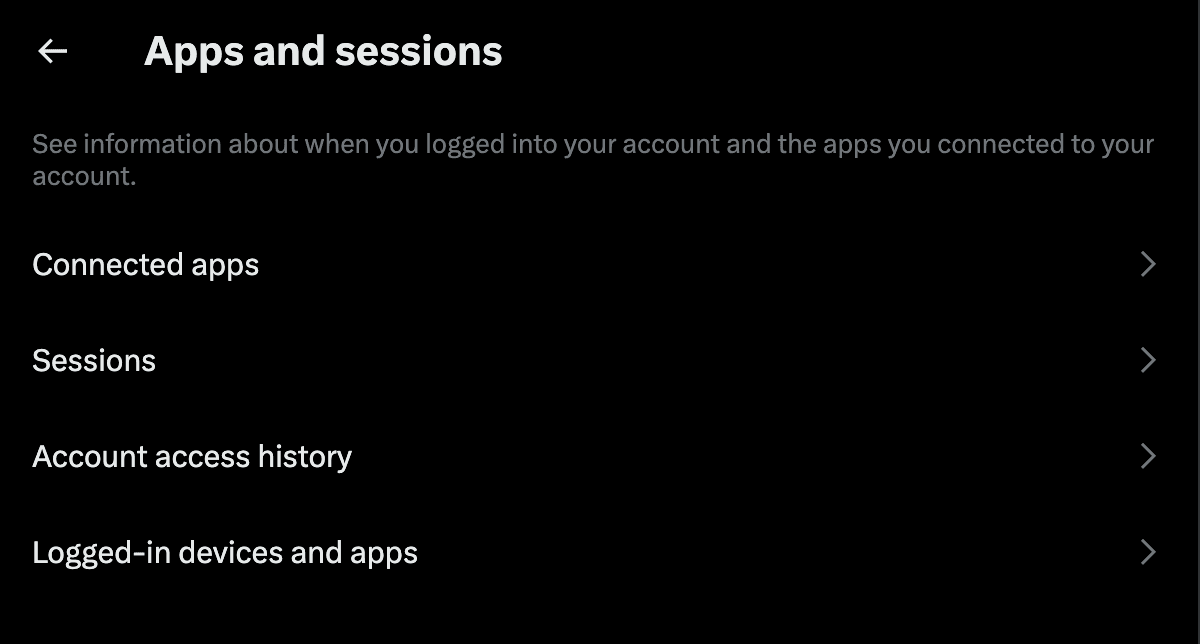
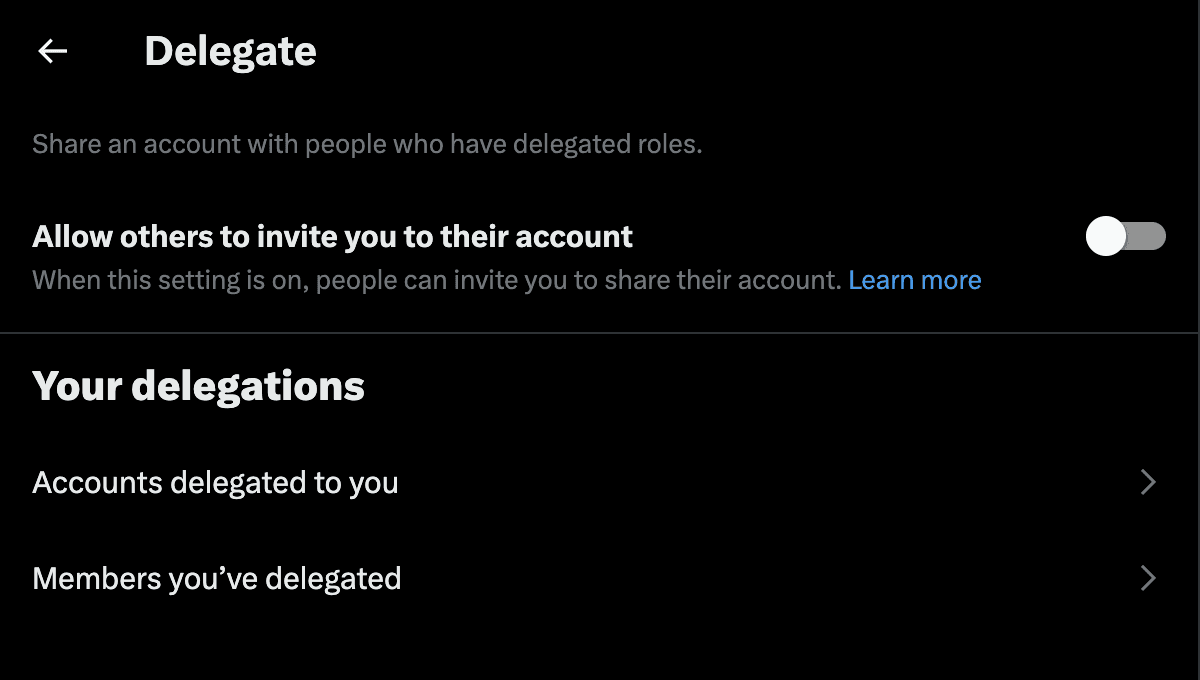
You will also want to check your delegation settings. Revoke delegation permissions for any accounts that you don’t recognize, or suspect may be compromised.
If you are unable to log in or reset your password, you’ll need to submit a request to regain access to your compromised account.
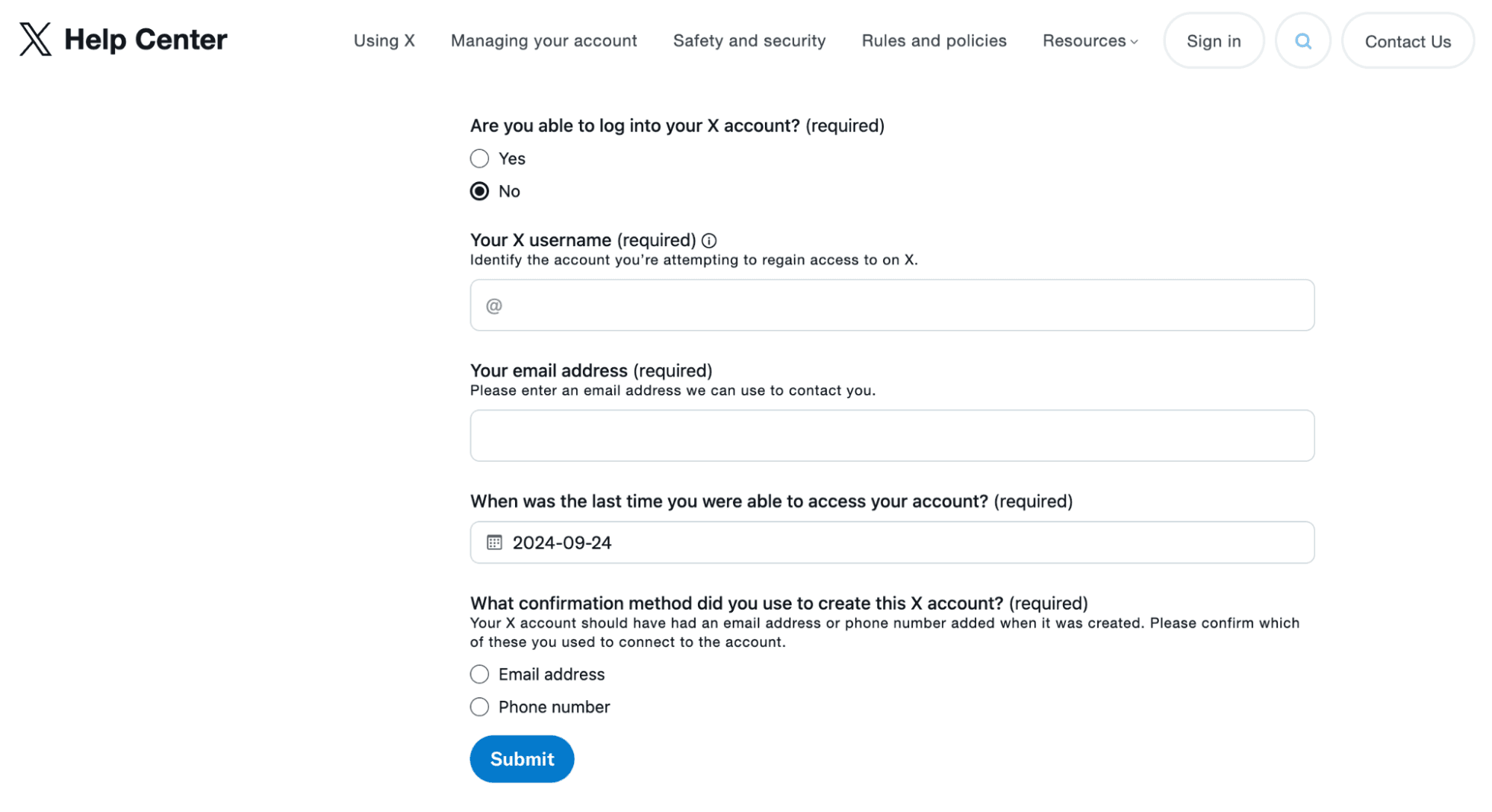
Step 2: Gather Information For the Regain Access Form
To regain access to your X account, you’ll need to submit a form through X.com. Ahead of submitting the form, gather all necessary information and documentation.
Required Information:
- Username of the X account.
- Email address linked to the X account.
- Phone number linked to the account (if applicable).
- Date of your last successful login.
Recommended Documentation:
- Government issued ID (for identity verification).
- Business card or relevant documentation confirming your affiliation with the brand.
- Any previous communication with Twitter support (support ID #).
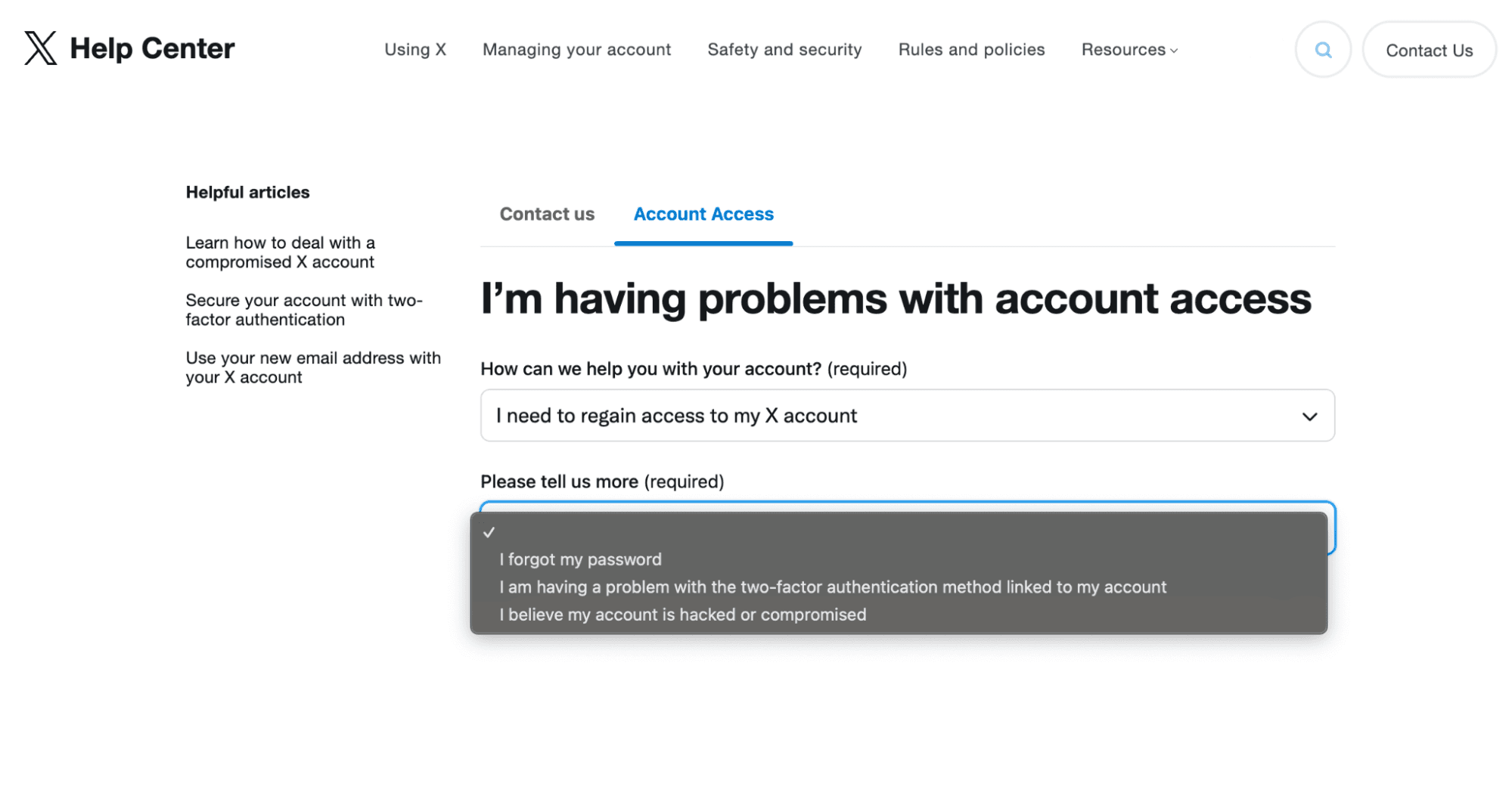
Step 3: Submit the Account Access Form
When you’ve gathered all of the information needed to submit your Regain Access form, go to the Regain Access page on X.com.
In the first dropdown menu, select “I need to regain access to my X account,” and in the second dropdown menu, select “I believe my account is hacked or compromised.”
When filling out the fields of the form, describe the problem you are having in detail, and include any support ticket numbers from previous communications with the X team.
You will also want to upload supporting evidence such as government ID, business cards, or screenshots to provide more information to the X team.
Step 4: Watch for Follow-Up Requests
Check your email inbox regularly for a follow-up from X. The team at X may request additional information to verify your identity or affiliation with the compromised profile. Staying on top of these emails will help you regain access to your X account as quickly as possible.
Best Practices to Keep Your X Account Secure
The best way to avoid your X account being compromised is to follow a few security best practices. These best practices are relevant not only to X, but to other social accounts like Discord, too.
To start, always be sure to use a strong, unique password that you update every 3 to 6 months. This password shouldn’t be used for anything else, and it shouldn’t refer to anything about your personal life – for example, don’t use your birthday, or the name of your pet. Be sure to also enable password reset protection.

Enable two-factor authentication (2FA) for added protection. This protects your X account by requiring you to provide a second form of confirmation that you are the rightful account owner.
For 2FA, use an authentication app ( like Google Authenticator or YubiKey) versus your phone number. Phone numbers are easily hacked with a SIM swap attack.
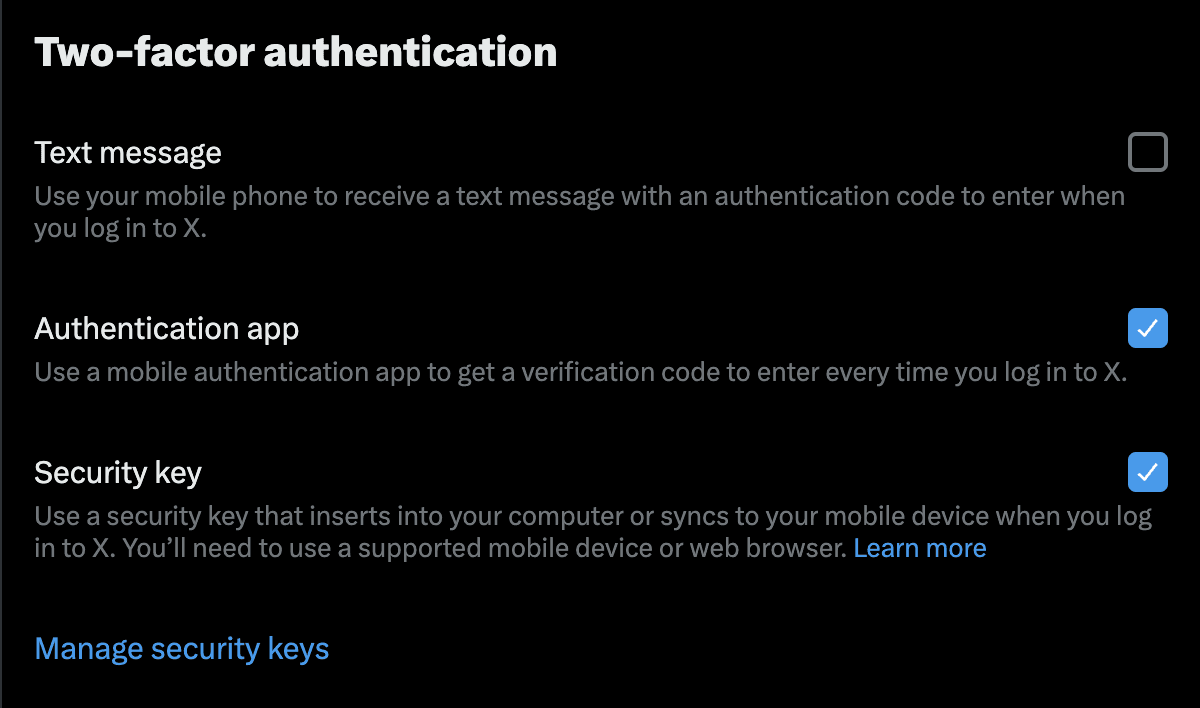
Be cautious of phishing attempts—avoid clicking on suspicious links or downloading unknown attachments. Regularly review connected apps and revoke access to any that seem unnecessary or untrustworthy.
If you are a team or a business, use account delegation instead of sharing login information. When login info is shared, 2FA typically has to be turned off, which is very dangerous. The benefit of account delegation is that multiple people can publish posts on X, and you can keep 2FA on.
Lastly, get into the habit of always logging out of your account on shared devices, and avoid logging in over public Wi-Fi without using a VPN.
Stay Protected on X
Recovering a compromised X account can be challenging, but taking fast action is key. By following the steps we’ve outlined above, you stop a hacker from taking further action, and regain control of your account.
Moving forward, follow best practices like using strong passwords and enabling two-factor authentication to protect your account from future attacks.
Do you want to keep your brand and community on X secure? Book a ChainPatrol demo to learn how we can monitor and protect your X accounts.