May 31, 2023
Automated Checks for Evidence of Suspicious Activity
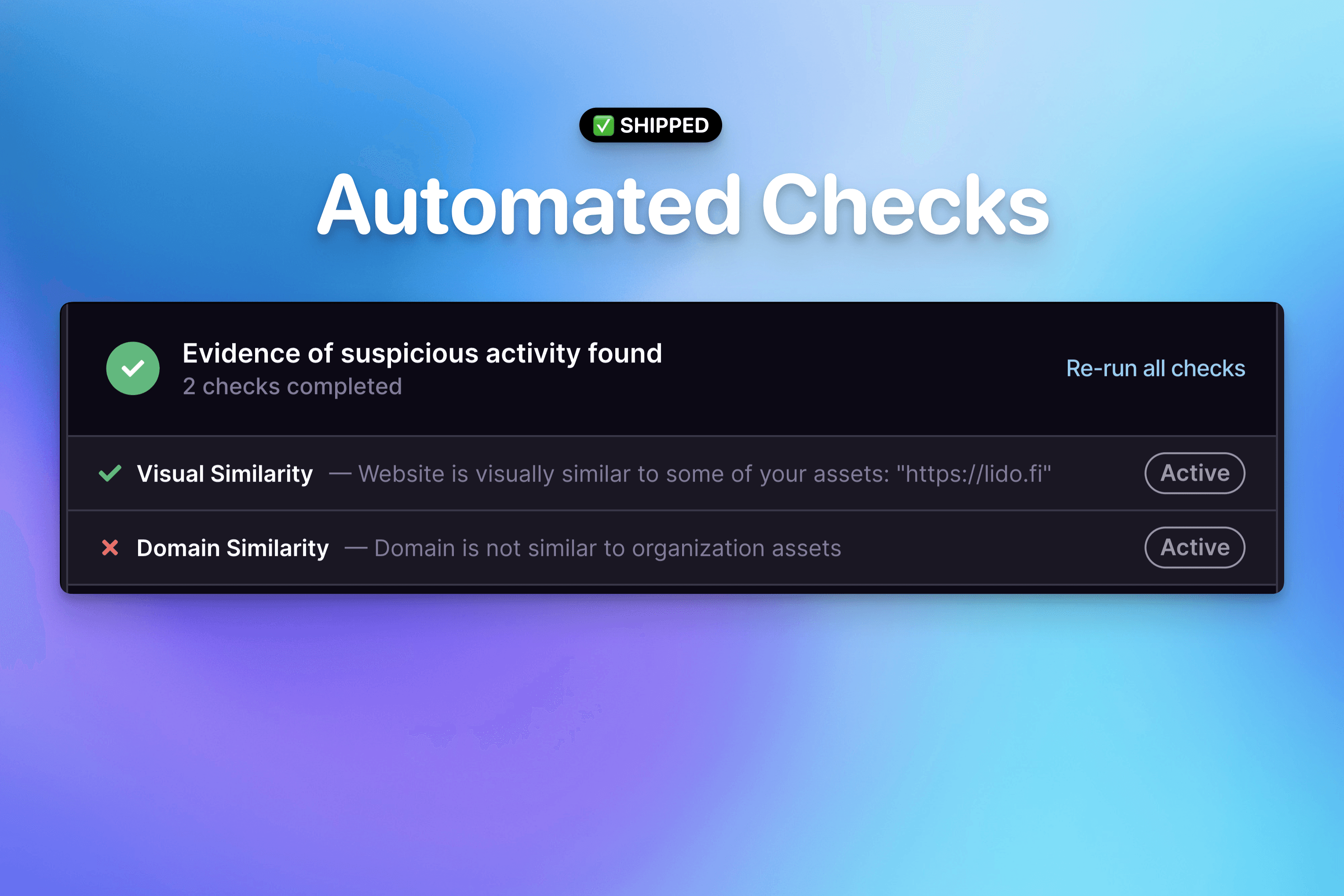


Automated checks are run when a new report is submitted to better detect suspicious activity on a webpage. Identify what techniques scammers are using to impersonate your brand and lure your community members into malicious transactions.
We've implemented the following checks so far:
Domain similarity - This check compares the reported URL against your organization's assets to determine if it is similar to any of your legitimate sites. Scammers will often use slight misspellings or visually similar characters to mislead users into thinking they are interacting with the legitimate site.
Visual similarity - This check compares the screenshot we generate for the reported site against the screenshots we've generated for your organization's assets. Often, fake sites will simply copy and paste the HTML from your legitimate site and make subtle edits, such as changing the Connect Wallet button or immediately requesting a malicious transaction from the user's wallet. We can detect this threat vector using this check and provide evidence to our reviewer staff members to expedite the review process.
We're just getting started with checks. We have tons of ideas for new checks like: detecting wallet drainers, checking for common scam kits, and much more.
Automated checks are run when a new report is submitted to better detect suspicious activity on a webpage. Identify what techniques scammers are using to impersonate your brand and lure your community members into malicious transactions.
We've implemented the following checks so far:
Domain similarity - This check compares the reported URL against your organization's assets to determine if it is similar to any of your legitimate sites. Scammers will often use slight misspellings or visually similar characters to mislead users into thinking they are interacting with the legitimate site.
Visual similarity - This check compares the screenshot we generate for the reported site against the screenshots we've generated for your organization's assets. Often, fake sites will simply copy and paste the HTML from your legitimate site and make subtle edits, such as changing the Connect Wallet button or immediately requesting a malicious transaction from the user's wallet. We can detect this threat vector using this check and provide evidence to our reviewer staff members to expedite the review process.
We're just getting started with checks. We have tons of ideas for new checks like: detecting wallet drainers, checking for common scam kits, and much more.
Automated checks are run when a new report is submitted to better detect suspicious activity on a webpage. Identify what techniques scammers are using to impersonate your brand and lure your community members into malicious transactions.
We've implemented the following checks so far:
Domain similarity - This check compares the reported URL against your organization's assets to determine if it is similar to any of your legitimate sites. Scammers will often use slight misspellings or visually similar characters to mislead users into thinking they are interacting with the legitimate site.
Visual similarity - This check compares the screenshot we generate for the reported site against the screenshots we've generated for your organization's assets. Often, fake sites will simply copy and paste the HTML from your legitimate site and make subtle edits, such as changing the Connect Wallet button or immediately requesting a malicious transaction from the user's wallet. We can detect this threat vector using this check and provide evidence to our reviewer staff members to expedite the review process.
We're just getting started with checks. We have tons of ideas for new checks like: detecting wallet drainers, checking for common scam kits, and much more.

ChainPatrol
© 2025 ChainPatrol Inc., All Rights Reserved

ChainPatrol
© 2025 ChainPatrol Inc., All Rights Reserved

ChainPatrol
© 2025 ChainPatrol Inc., All Rights Reserved